Optiv’s Cloud Security Architecture Assessment for AWS
Businesses are always looking for the best practices to take when migrating their assets to the cloud. This includes assessing current technology and workloads for cloud compatibility, taking an inventory of all sanctioned and unsanctioned applications and orchestrating an enterprise-wide cyber security effort to eliminate siloes in the organization.
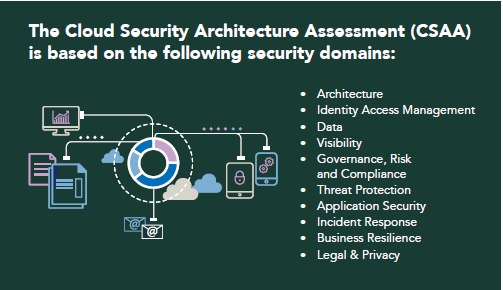
Optiv’s Cloud Security Architecture Assessment (CSAA) for AWS facilitates a meeting between a client’s key stakeholders and our industry experts to identify existing challenges, define business goals, maturity level and outcomes and build an actionable roadmap to enable security program success. By applying a holistic approach that accounts for security across the stack and harmonizing siloes in the organization, we create the efficiency and agility necessary for you to proactively secure and operationalize your business.
How the assessment works:
- PRIOR TO THE ENGAGEMENT: Optiv consultants provide an in-depth cloud security questionnaire tailored to each engagement as well as a list of functional areas to be interviewed during the assessment.
- ONSITE ACTIVITIES: Optiv performs deep discovery through stakeholder meetings and data collection focusing on business drivers, priorities and key technical and security requirements. Our architects evaluate your current technology environment and conduct a gap analysis of your existing cloud security implementation. Our typical program includes collaborative whiteboard sessions, review of existing resources and processes, and an automated compliance and visibility scan.
- CLOUD SECURITY ARCHITECTURE ASSESSMENT (CSAA): Optiv reviews the results of the onsite discovery and performs a post engagement gap analysis. We leverage our vast database of critical controls that are regularly updated to assess both the hygiene of the platform and the maturity of the security efforts around cloud to quickly bring clarity and visibility to the enterprise security team.
- BEYOND CSAA: To help realize the roadmap produced from the engagement, you have the option to continue to leverage our capabilities and subject matter experts on staff. As an advisor and architect, we will activate and guide the recommended cloud security program on your behalf through implementation of our secure cloud reference architecture and deployment of the correct technology needed.
With Optiv’s CSAA, customers can:
- Improve performance, scalability and time to value while securely migrating workloads to the cloud
- Achieve long term cost savings by consolidating project requirements, technologies and resources across all cloud business initiatives and projects.
- Reduce risk of security breaches and increase compliance with regulatory mandates